Double DKIM: Difference between revisions
Created page with "Category:InboxSys Category:E-Mail_analysis Category:Authentication thumb|Typical double DKIM warning InboxSys rolls out Double DKIM testing feature! If you see additional DKIM warnings in your InboxSys account, here is why. As you may or may not know it’s best practice to align your domains when sending emails, such as your bounce domain, sender from domain, hostname, im..." |
No edit summary |
||
| (11 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:InboxSys]] | [[Category:InboxSys]] | ||
[[Category:Deliverability]] | |||
[[Category:E-Mail_analysis]] | [[Category:E-Mail_analysis]] | ||
[[Category:Reporting]] | |||
[[Category:Authentication]] | [[Category:Authentication]] | ||
[[ | It commonly is best practice to [[Alignment|align]] your domains when sending emails, such as your envelope-from domain ([[RFC5321.MailFrom]]), Header-From domain ([[RFC5322.From]]), [[Domain_Alignment#Hostname_/_HELO/EHLO|hostname]], [[DomainKeys_Identified_Mail_(DKIM)#Public_and_private_key|DKIM signing domain]] and [[Domain_Alignment#Link-_and_imagedomains_/_Sender_domains|imagelink and link tracking domain]], meaning that ideally all these should be on the same [[Responsible domain|responsible domain]] name. | ||
[[ | |||
Although this is best practice, this is an unrealistic point of view. In reality, often Email Service Providers require you to use their domain for your bounces, for example because that makes processing bounces and [[feedbackloop]] data easier. In cases where you can use your own domain for RFC5321.MailFrom and RFC5322.From, HELO/EHLO and hostnames are often still ESP-owned - and thus different - domains. This is where double DKIM comes in. | |||
=Functionality= | |||
In the common [[DKIM]] standard ([https://www.rfc-editor.org/rfc/rfc6376.html|RFC 6376]) there is no mentioning of which domain to use as signing domain, but taking [[DMARC]] and alignment into consideration, it is recommended to sign at least with the Header:-From domain as DKIM signing domain. Messages can also be signed with - for example - the envelope-from domain or the hostname. In fact, as long as you own a domain, you can use it as DKIM signing domain. | |||
RFC 6376 also doesn't mention how often you can sign a single E-Mail with different signing domains. It's possible to sign a single message multiple times with the same domain, or with a different domain. One good example of a use case is when you would like to DKIM sign your message with ed25519 keys, but you want a fallback for hosts that only understand RSA. In that case, it's possible to sign the message twice with the same signing domain, but with the two different type of keys. | |||
If the hostname and the sender domains, or the sender domains and link domains, are completely different domains, the message should be DKIM signed once for each domain used, with different signing domains and in the best case, also different keys and [[DomainKeys_Identified_Mail_(DKIM)#Selector|selectors]]. | |||
Senders who sign with multiple signing domains and want ed25519 ''plus'' RSA-fallback for each domain quickly produce headers full of DKIM signatures. It's recommended not to create more than 4 DKIM signatures per message. | |||
<strong>So, is it, and why is it, | <strong>So, is it, and why is it, recommended to sign Double with DKIM, even if all your domains align perfectly?</strong> | ||
Apart from declaring which domains may be used in this message, the | Apart from declaring which domains may be used in this message, the second DKIM signature is also meant as a fallback. If - for example - there is a fault on the [[DNS]] for one signing domain, the message still has a valid DKIM signature on the other, even if [[Domain_Alignment#DKIM_alignment|DKIM doesn't align anymore]] in this case. | ||
Understanding the importance of Double DKIM is the first step, beyond that there is a preferred way of signing your DKIM signatures. | Understanding the importance of Double DKIM is the first step, beyond that there is a preferred way of signing your DKIM signatures. | ||
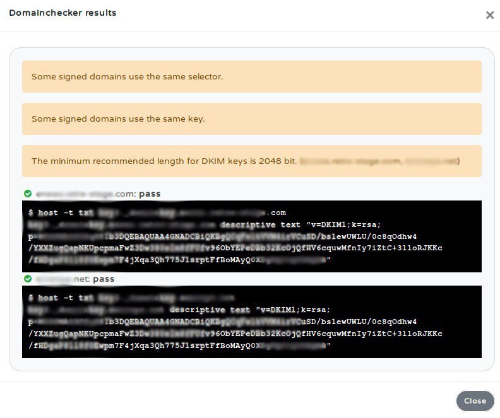
# For multiple domains, use separate | # For multiple domains, use separate selectors. | ||
# Use different | # Use different keys when using multiple domains. | ||
# The | # The minimum recommended length for DKIM keys is 2048 bit. | ||
# [[DKIM key rotation|Rotate keys regularly]]. | |||
==Summary== | ==Summary== | ||
The key | [[File:Double-dkim.png|thumb|Typical double DKIM warning]] | ||
The key takeaway from this is to remember, especially when using multiple domains in your E-Mails, to take into consideration Double DKIM. By doing this you shall be better aligned and your configuration will be looked upon favorably by some filters & ISPs, which could mean improved Deliverability rates. | |||
=Double DKIM in InboxSys= | |||
InboxSys checks for Double DKIM in the [[:Category:E-Mail_analysis|E-Mail analysis]] section. | |||
* Messages with a single DKIM record are yellow | |||
* Messages with a double DKIM record are green if | |||
** both signatures pass the check, | |||
** keys are different and | |||
** selectors are different. | |||
Latest revision as of 15:13, 7 October 2024
It commonly is best practice to align your domains when sending emails, such as your envelope-from domain (RFC5321.MailFrom), Header-From domain (RFC5322.From), hostname, DKIM signing domain and imagelink and link tracking domain, meaning that ideally all these should be on the same responsible domain name.
Although this is best practice, this is an unrealistic point of view. In reality, often Email Service Providers require you to use their domain for your bounces, for example because that makes processing bounces and feedbackloop data easier. In cases where you can use your own domain for RFC5321.MailFrom and RFC5322.From, HELO/EHLO and hostnames are often still ESP-owned - and thus different - domains. This is where double DKIM comes in.
Functionality
In the common DKIM standard (6376) there is no mentioning of which domain to use as signing domain, but taking DMARC and alignment into consideration, it is recommended to sign at least with the Header:-From domain as DKIM signing domain. Messages can also be signed with - for example - the envelope-from domain or the hostname. In fact, as long as you own a domain, you can use it as DKIM signing domain.
RFC 6376 also doesn't mention how often you can sign a single E-Mail with different signing domains. It's possible to sign a single message multiple times with the same domain, or with a different domain. One good example of a use case is when you would like to DKIM sign your message with ed25519 keys, but you want a fallback for hosts that only understand RSA. In that case, it's possible to sign the message twice with the same signing domain, but with the two different type of keys.
If the hostname and the sender domains, or the sender domains and link domains, are completely different domains, the message should be DKIM signed once for each domain used, with different signing domains and in the best case, also different keys and selectors.
Senders who sign with multiple signing domains and want ed25519 plus RSA-fallback for each domain quickly produce headers full of DKIM signatures. It's recommended not to create more than 4 DKIM signatures per message.
So, is it, and why is it, recommended to sign Double with DKIM, even if all your domains align perfectly?
Apart from declaring which domains may be used in this message, the second DKIM signature is also meant as a fallback. If - for example - there is a fault on the DNS for one signing domain, the message still has a valid DKIM signature on the other, even if DKIM doesn't align anymore in this case.
Understanding the importance of Double DKIM is the first step, beyond that there is a preferred way of signing your DKIM signatures.
- For multiple domains, use separate selectors.
- Use different keys when using multiple domains.
- The minimum recommended length for DKIM keys is 2048 bit.
- Rotate keys regularly.
Summary
The key takeaway from this is to remember, especially when using multiple domains in your E-Mails, to take into consideration Double DKIM. By doing this you shall be better aligned and your configuration will be looked upon favorably by some filters & ISPs, which could mean improved Deliverability rates.
Double DKIM in InboxSys
InboxSys checks for Double DKIM in the E-Mail analysis section.
- Messages with a single DKIM record are yellow
- Messages with a double DKIM record are green if
- both signatures pass the check,
- keys are different and
- selectors are different.